How to Fix Deviant Art Invalid Certificate Chrome Error
A new malicious application tries to disguise itself equally the Google Chrome browser to fool victims into entering their payment card details. The app is still active at the fourth dimension of writing and sends collected user details to an AOL email address.
Discovered today past MalwareHunter, this application goes in a higher place and beyond of what other card stealers have attempted, almost of which are half-baked efforts, oft easy to recognize equally malicious applications cheers to their quirky graphics and misaligned designs.
This app, named "Betaling - Google Chrome.exe", tries to pass as the Google Chrome browser and does a expert job at information technology. Betaling ("Payment" in Dutch) uses the standard Chrome icon and window layout, consummate with an accost bar, and even an HTTPS lock icon to play tricks users they're on a real website.
![]()
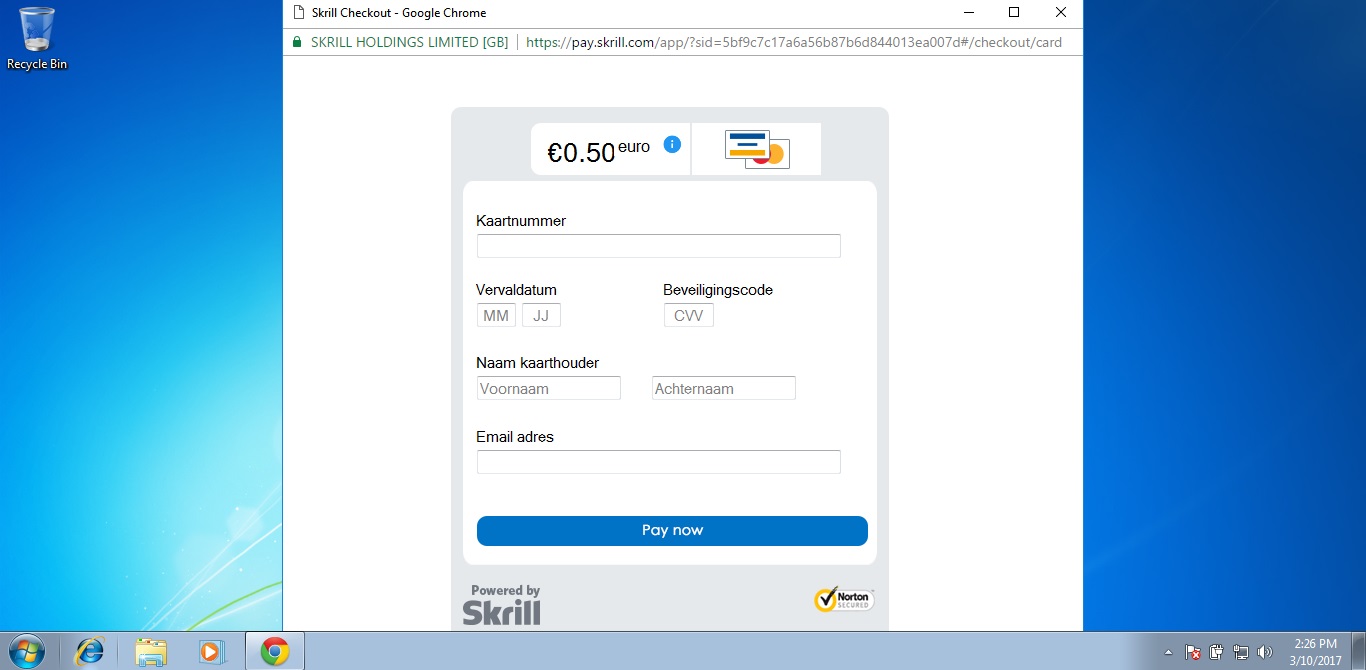
Betaling giveaways!
Betaling isn't a perfect Google Chrome, though, as at that place are a few clues that experienced users tin can spot.
For starters, the malicious app requires users to have installed a minimum version of .Cyberspace Framework 4.0 or higher, a requirement the real Google Chrome never had.
Second, the app also uses the standard Windows eight/eight.i/ten Metro style, even when running on a Windows vii PC.
Third, while Betaling tries to fox users into thinking it's the real Chrome, outside of the lock icon and the address bar, the rest of the Chrome UI is missing, such as the tab bar, the menu, Chrome buttons, and others.
Last but not least, simply the shut push button works. Users tin can't resize the window, can't minimize it, tin can't make it fullscreen, can't drag it, and tin't enter a new URL.
Betaling is currently targeting the Netherlands
Withal, much less sophisticated malware has been able to infect hundreds or thousands of users in the by, which means Betaling and its UI tin be quite effective.
Several security researchers who've taken a look at Betaling were impressed by its carefully crafted design. Non-infosec people idea Betaling was a phishing page loaded within a Chrome browser, and but some fourth dimension later realized they weren't looking at a Chrome window to begin with.
Currently, Betaling's interface is only bachelor in Dutch, which reveals the malware'south current target.
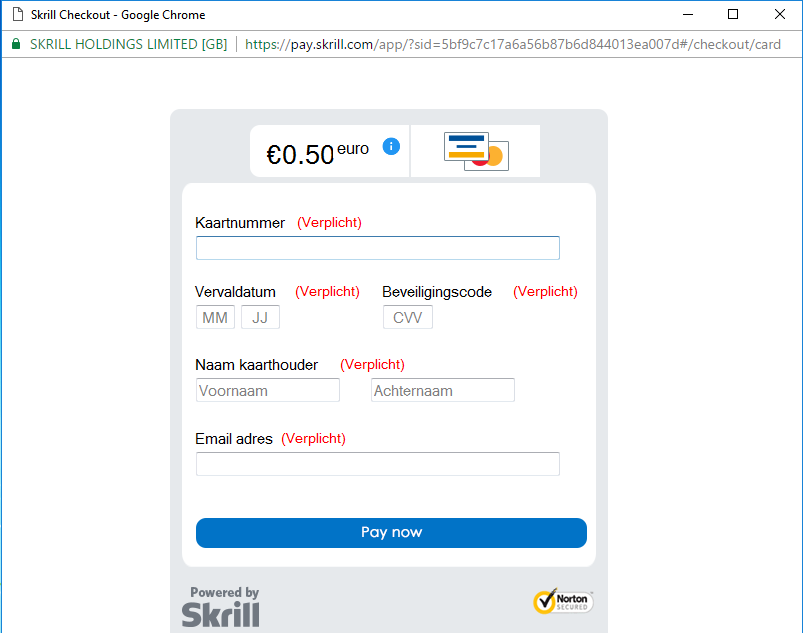
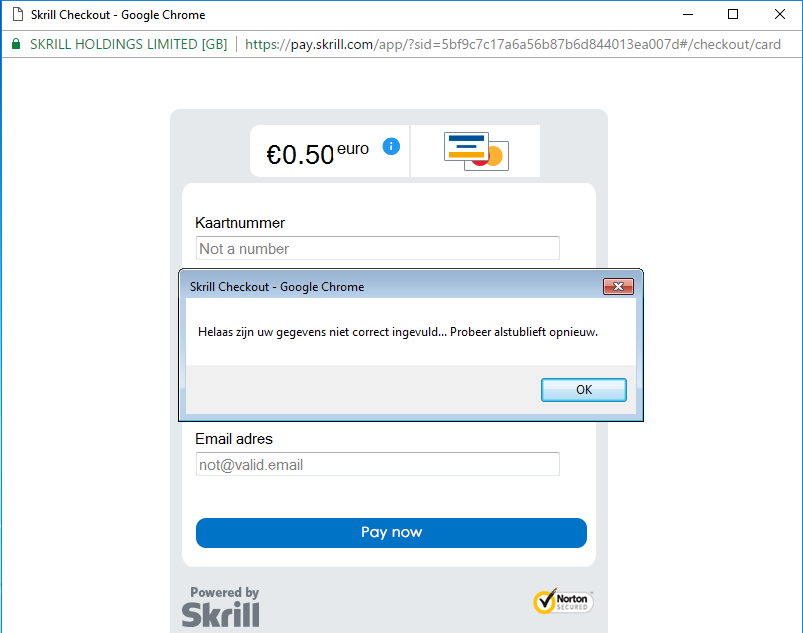
The form displayed within the simulated Chrome window isn't bullheaded to user input like near phishing pages, and some data validation takes identify, yielding two sorts of errors.
| | |
Hacking back
If correct the data is entered, Betaling collects all information and sends information technology to an AOL email address at whatsapp.hack@aol.com.
This email accost was discovered when security researchers analyzed the awarding'due south source lawmaking. Accessing its inbox, they've discovered contempo logs, including the test data entered during Bleeping Reckoner's tests, significant the app works only fine.
Likewise recent logs from Betaling, researchers likewise found logs from an unidentified keylogger. These logs went back as far as January 2016 and included details from victims from all over the earth.
"It'south been long since he got any [keylogger] logs," said a security researcher that goes past the name of Guido, who also analyzed the malware.
Guido, who already reported the malware to government, says the initial entries for the keylogger logs independent a series of recurring electronic mail addresses. Common sense dictates these are the writer'southward own emails, which he used for testing, during the keylogger's development and subsequent rollout.
These two emails, patrick***@live.nl and patrick*******@gmail.com, are also linked to accounts on the Spokeo social network.
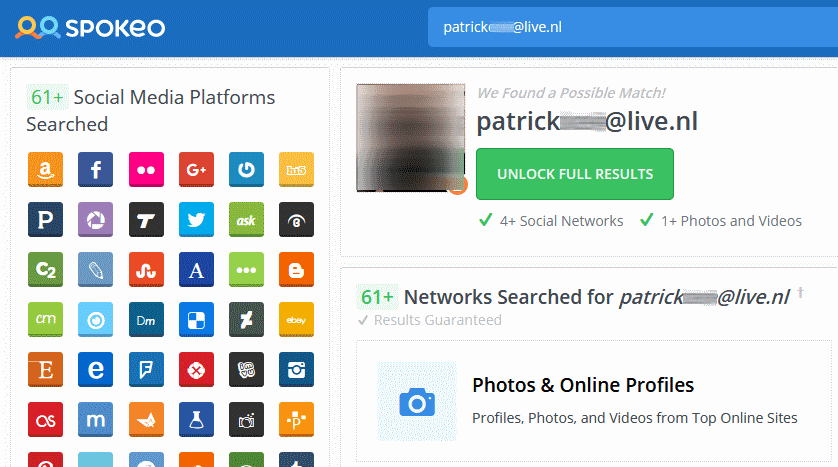
Furthermore, Betaling's PDB file includes a compilation path of "C:\Users\Patrick\", and the Betaling EXE file is also self-signed by an invalid document authority named "CN = DESKTOP-PC\Patrick".
Both mentions of the "Patrick" proper name are consequent with the ii electronic mail addresses found in the keylogger'south first log entries. It's now up to government to investigate and determine if the owner of the two e-mail addresses is backside Betaling or not.
Furthermore, Guido told Bleeping Computer that in August 2016, "Patrick" sent an electronic mail from the AOL account to ankit******@speedpost.net asking for help with a "stealer" that was having several bugs. It'south currently unknown if he was referring to Betaling in its early stages of evolution, or a dissimilar stealer altogether.
SHA256 hash (VirusTotal link): 42e2b2e17ff85fc1a399e712a488c1ed35af3b7b8b061bdde86ec4732138254c
Source: https://www.bleepingcomputer.com/news/security/credit-card-stealer-disguises-as-google-chrome-browser/
0 Response to "How to Fix Deviant Art Invalid Certificate Chrome Error"
Post a Comment